Elliptic Curve Cryptography
Elliptic Curve
Assume a field $\Bbb{K}$, and the field's characteristic, $char(\Bbb{K}) \neq 2,3$, then an Elliptic Curve over the field can be described as the equation:
$E(x, y): y^2 = x^3 + ax + b$
There is a singular point $P(x_p, y_p)$, if
And substitute in $E(x,y)$
Such that if $4a^3+27b^2 \neq 0$ then the curve $E(x,y)$ is no-singular.
At last, here is the definition of elliptic curve:
with $\mathcal{O}$ the point at $\infty$. A group over elliptic curves can be defined as below:
the elements of the group are the points of an elliptic curve
the identity element is the point $\mathcal{O}$
the inverse of a point P is the one symmetric about the x-axis
addition: given 3 aligned, non-zero points P, Q and R, their sum P+Q+R=0
Addition
Given 3 aligned, non-zero points P, Q and R, their sum P+Q+R=0
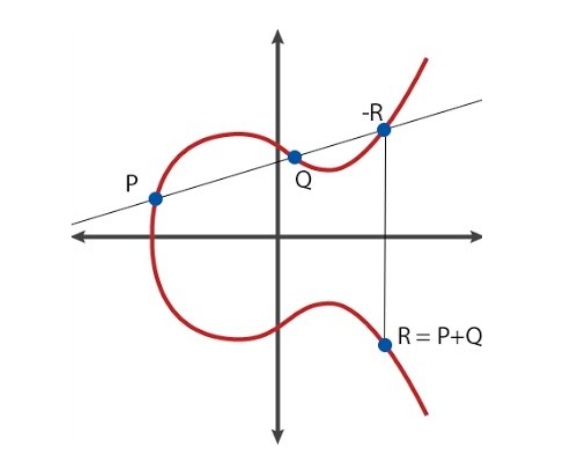
Elliptic curve (E): $y^2 = x^3 + ax + b$
Line (L): $y=mx+n$
The intersection points of (E) and (L) are the solutions to the equation below:
According to Vieta’s Formulas
Assume 2 intersection points P, Q are already known, then the third intersection point -R, $P(x_R, -y_R)$,
So the point R, $P(x_R, y_R)$:
If $x_P \neq x_Q$,
If $x_P = x_Q$
Multiplication
$nP = P + P + ... + P$
Elliptic Curves over finite fields
In cryptography the finite field is usually a set of integers modulo $p$, where $p$ is a prime number. It is denoted as $GF(p)$ or $\Bbb{F}_p$, and $char(\Bbb{F}_p) = p$. Then an elliptic curve can be defined as:
where $\mathcal{O}$ is still the point at $\infty$, $a$ and $b$ are two integers in $\Bbb{F}_p$, and $char(\Bbb{F}_p)=p \neq 2,3$
What is an elliptic curve cofactor?
https://crypto.stackexchange.com/questions/56344/what-is-an-elliptic-curve-cofactor
In cryptography, an elliptic curve is a group which has a given size n. We normally work in a subgroup of prime order r, where r divides n. The "cofactor" is $h=n/r$.
For every point $P$ on the curve, the point $hP$ is either the "point at infinity", or it has order $r$; i.e., when taking a point, multiplying it by the cofactor necessarily yields a point in the subgroup of prime order $r$.
SafeCurves: choosing safe curves for elliptic-curve cryptography https://safecurves.cr.yp.to/
Standard curve database
https://github.com/J08nY/std-curves
https://neuromancer.sk/std/
- P-384: https://neuromancer.sk/std/nist/P-384
What is an elliptic curve?
https://www.bilibili.com/video/BV1gN411o7un/?spmidfrom=333.337.search-card.all.click&vd_source=8d17b3ae547585ed3fea79027e6d20eb
Given a polynomial equation $f(x_1, x_2, ..., x_r) = 0$ with integer coefficients (i.e., a diophantine equation), we can ask three questions:
Can we determine if there are rational or integral solutions?
In the affirmative case, can we find such a solution?
Can we describe all such solutions?
(Hilbert's Tenth Problem over $Z$) Is there a Turing machine to decide if $f=0$ has solutions in $Z$ (Davis, Matiyasevich Putnam, Robinson: No) .
Examples of diophantine equation:
$9(x^2 + 7y^2)^2 - 7(u^2 + 7v^2)^2 = 2$
Elliptic Curve Point Addition
https://www.rareskills.io/post/elliptic-curve-addition
Cryptography uses elliptic curves over finite fields, but elliptic curves are easier to conceptualize in a real cartesian plane.
the identity element (which is the only element that can be the inverse of itself)
Elliptic curve point multiplication
https://en.wikipedia.org/wiki/Ellipticcurvepoint_multiplication
Constant time Montgomery ladder
The security of a cryptographic implementation is likely to face the threat of the so called timing attacks which exploits the data-dependent timing characteristics of the implementation.
Identity element https://en.wikipedia.org/wiki/Identity_element